Understanding Memory Safety
Memory safety is a broad concept encompassing various techniques and methodologies used to prevent software from improperly accessing or manipulating memory. Memory-related vulnerabilities have long been a leading cause of security flaws in software, resulting in issues ranging from crashes to security breaches. Understanding memory safety in depth involves knowing both the causes of memory issues and how modern approaches aim to eliminate them.
Memory safety is a system’s ability to prevent software from inadvertently or maliciously accessing incorrect memory locations. These errors are primarily seen in systems written in low-level languages (e.g., C/C++) but can appear in any environment where explicit memory management is required. Failing to enforce memory safety can lead to vulnerabilities like buffer overflows, which hackers can exploit to execute arbitrary code, corrupt memory, or crash systems.
Common Memory Safety Violations
Buffer Overflows
Buffer overflows happen when data is written beyond the boundary of a fixed-size buffer. This overwrites adjacent memory, which can corrupt program behavior, crash the system, or allow an attacker to overwrite control data (e.g., return addresses, function pointers) to hijack execution flow.
Example
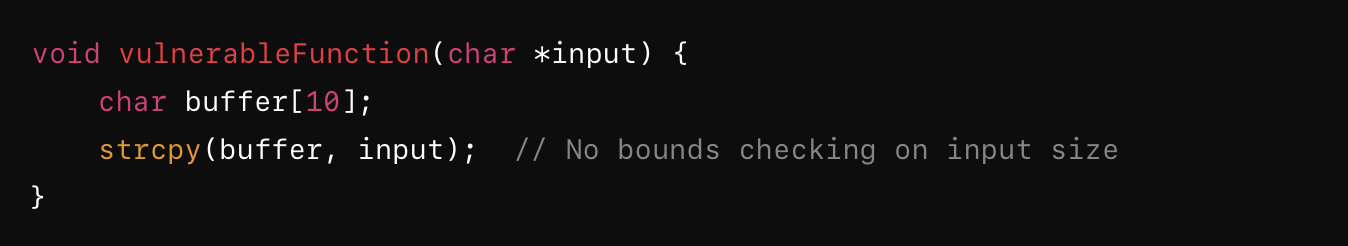
Consider a stack-based buffer overflow:
If the input is longer than 10 characters, strcpy will write past the bounds of buffer, potentially overwriting important control data on the stack, such as the return address of the function. By crafting a malicious input, an attacker can overwrite the return address to point to shellcode, executing arbitrary commands.
Heap Corruption (Heap Overflows and Double Free)
Unlike stack overflows, heap overflows involve dynamically allocated memory. If a program writes beyond the bounds of a heap-allocated buffer, it can corrupt adjacent heap metadata or program data. Additionally, double-free errors, where memory is deallocated twice, can cause heap corruption by altering memory allocation metadata, leading to undefined behaviour.
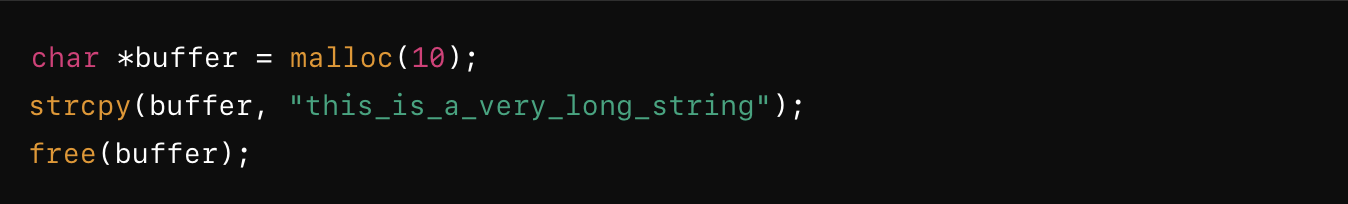
The code above overflows the 10-byte buffer and can potentially corrupt adjacent heap structures. After free(buffer), a double free of the same buffer would cause the heap's memory management functions to behave unpredictably, opening the door to potential heap exploitation.
Use-After-Free
This occurs when memory is accessed after it has been deallocated. Once memory is freed, it may be reassigned to another process or variable. Using it after deallocation can cause corrupted data to be read or written, or in some cases, allow for attacker-controlled memory to be accessed.
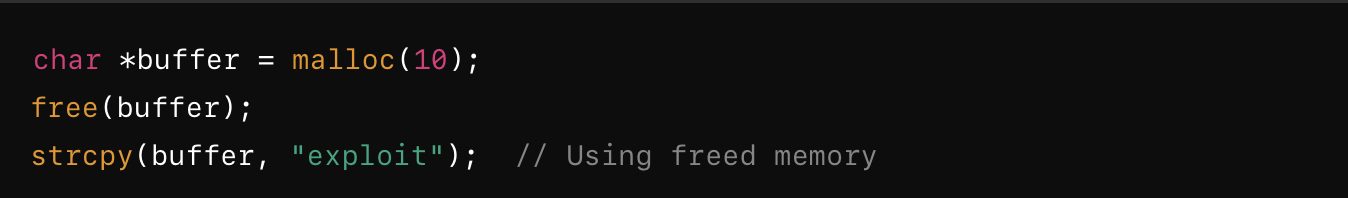
Even though buffer is freed, the program still attempts to use it. If the memory area is reused by the system, an attacker could control what gets placed in that memory location.
Dangling Pointers
Dangling pointers are pointers that reference memory that has already been freed. Accessing such memory can result in corrupted data or crashes, and attackers can exploit this to manipulate program behaviour.
Null Pointer Dereferencing
This occurs when a program attempts to access or modify memory through a pointer that is NULL, leading to a crash or program termination
